General Idea on Cloud Security
Cloud technology is shaping our world today. Most organizations in the world today has adapted cloud technology. Although, most of them implemented hybrid solutions as in having both cloud infrastructure and local on site infrastructure.
With the ever-changing technology, organizations are trying to figure out how their organization can keep up. A notable example is the interconnected mobile technology on the cloud, such as Social Networking. The usage of Social Networks are vastly increasing due to the increasing amount of internet-connected devices from numerous users. The rapid growth of this trend is due to the convenient ease of accessing information that is stored on the cloud about people who mattered to them anywhere and anytime. Another trend that is worth mentioning is the ability to play multiplayer games in a cross platform. These examples shows that having a data stored on the cloud enables ease of access to its users and therefore increasing mobility and efficiency. In an organization, mobility and efficiency is crucial in order to save both time and resources. A lot of organizations have considered this as their priority, but there are still a handful of organization that did not consider this at all and scrapped it altogether. Monetizing data they have on their user by offering them products based on their preferences is also one of the things that organizations are trying to figure out. Having to use this marketing strategy might cause them to stumble upon privacy breach laws on their users' respective country, as well as the risk of having their data unsecure which leads to data leakage.
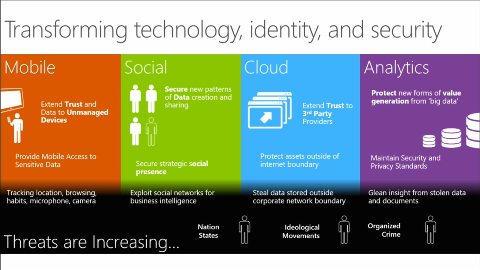 With the huge amount of users with internet-connected devices, storing valuable data on their unsecure devices and infrastructure will increase the probability of security breaches through security flaws. These security flaws are usually but not always unpatched Java applets, vulnerable Flash plugins, and social phishings using click baits and phishing datas. These security breaches will result in stolen encrypted keys, causing loss of encrypted sensitive datas. Common motives to steal data off organizations are intellectual property theft, espionage, currency theft, and PII/PHI.
With the huge amount of users with internet-connected devices, storing valuable data on their unsecure devices and infrastructure will increase the probability of security breaches through security flaws. These security flaws are usually but not always unpatched Java applets, vulnerable Flash plugins, and social phishings using click baits and phishing datas. These security breaches will result in stolen encrypted keys, causing loss of encrypted sensitive datas. Common motives to steal data off organizations are intellectual property theft, espionage, currency theft, and PII/PHI.
Entrusting sensistive datas on trusted cloud providers will prevent the aforementioned data losses from happening. By letting these cloud providers handling operational and security responsibility, datas that organizations store in the cloud will be much more secure and they will be able to focus on more important things.
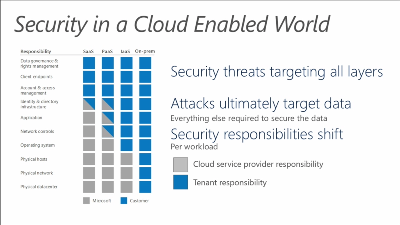 This graph shows the responsibilities of the tenant and the cloud service provider on four different services. As shown on the graph, the tenant had less responsibilities when SaaS (Software as a Service), PaaS (Platform as a Service), and IaaS (Infrastructure as a Service) is used. This is due to the responsibilities of the tenant are handed to the cloud service provider. Handing responsibilities means that the tenant is able to focus on more important matters and not wasting time on simple technical matters. By using one of the cloud services, whether it is SaaS, PaaS, or IaaS, means that you as the tenant are entrusting your supposed responsibility to your cloud service provider. It is also mean that you are entrusting the security of your data to the cloud service provider.
This graph shows the responsibilities of the tenant and the cloud service provider on four different services. As shown on the graph, the tenant had less responsibilities when SaaS (Software as a Service), PaaS (Platform as a Service), and IaaS (Infrastructure as a Service) is used. This is due to the responsibilities of the tenant are handed to the cloud service provider. Handing responsibilities means that the tenant is able to focus on more important matters and not wasting time on simple technical matters. By using one of the cloud services, whether it is SaaS, PaaS, or IaaS, means that you as the tenant are entrusting your supposed responsibility to your cloud service provider. It is also mean that you are entrusting the security of your data to the cloud service provider.